| Lesson 4 | The Internet, VPNs, intranets, and extranets |
| Objective | Distinguish between the Internet, VPNs, intranets and extranets. |
Internet, Intranets, and Extranets
The realm of digital communication and information sharing has witnessed profound evolution with the advent of technologies such as the Internet, Intranets, and Extranets. While these terms are occasionally used interchangeably by the uninitiated, they are, in fact, distinct in their design, purpose, and scope. This analysis aims to elucidate the fundamental differences among these three digital domains.
Internet
The Internet is a network of networks linking computers all over the world. The content on the Internet is located in independently owned computers called servers. Servers are linked to regional networks, which in turn connect to the core of the Internet.
These points of connection are called network access points (NAPs). This image illustrates Internet topology.
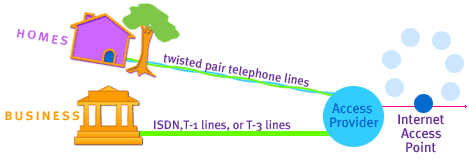
There are many ways that a company can connect to the Internet. Many home users connect via PC modems that use twisted-pair telephone lines.
For faster connections, businesses and a few home users use ISDN, T-1 lines, or T-3 lines. Regardless of speed, all lines to the Internet are routed through local access providers. Local access providers use the user's Internet access provider to connect to one of the Internet's access points.
VPNs
As shown here, a Virtual Private Network or VPN is a private network that is configured within a public network. It is constructed by using public wires to connect individual computers in a simulated private network.
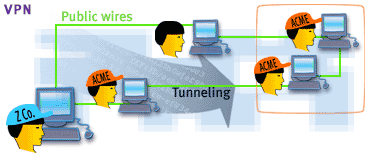
A VPN enables IP traffic to travel securely over a public TCP/IP network by encrypting the traffic from one network to another. This encrypting technique is called tunneling. Tunneling ensures that only authorized users can access the network and that the data cannot be intercepted. Basically, this means that company employees can access their company's network from remote distances without risk to network security.
- Transmission Control Protocol/Internet Protocol: A communications protocol developed under contract from the U.S. Department of Defense to internetwork dissimilar systems. Invented by Vinton Cerf and Bob Kahn, this de facto UNIX standard is the protocol of the Internet and has become the global standard for communications. TCP provides transport functions, which ensures that the total amount of bytes sent is received correctly at the other end. IP provides the routing mechanism. TCP/IP is a routable protocol, which means that all messages contain not only the address of the destination station, but also the address of a destination network. This allows TCP/IP messages to be sent to multiple networks within an organization or around the world, hence its use in the Internet.
Intranets
Intranets are essentially private Internets, or Internets inside of an organization. As this image shows, they enable organizations to use the Web as a convenient, low-cost channel for information sharing and distribution among an organization's employees and its other members.
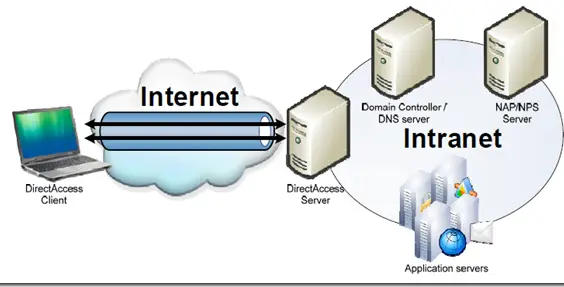
An intranet's Web sites look and act just like any Internet Web site. The main difference is that the firewall surrounding an intranet prevents unauthorized access.
What is a Firewall
A firewall is a method for keeping a network secure. It can be implemented in a single router that filters out unwanted packets, or it may use a combination of technologies in routers and hosts. Firewalls are widely used to give users access to the Internet in a secure fashion as well as to separate a company's public Web server from its internal network. They are also used to keep internal network segments secure.
For example, a research or accounting subnet might be vulnerable to snooping from within.
Extranets
Extranets are like intranets insofar as they are networks that are not available to the general public (like the Internet). But whereas an intranet resides behind a firewall and is accessible only to people who are members of the same company or organization, an extranet provides accessibility to a predetermined set of outsiders. You can think of an extranet as an Intranet between organizational partners. This image illustrates an extranet.
Extranets are becoming a popular means for business partners to exchange information.
Extranets are becoming a popular means for business partners to exchange information.
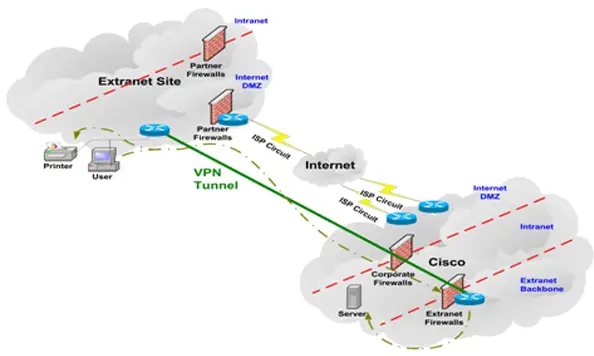
Question: How are the Internet, intranets, and extranets similar and how do they differ?
Answer: Intranets and extranets use similar protocols and equipment as the Internet, as all are TCP/IP-based networks. But intranets and extranets are limited in their physical distribution and by their security hardware and software.
The following paragraph discusses the networking systems for particular business needs.
Answer: Intranets and extranets use similar protocols and equipment as the Internet, as all are TCP/IP-based networks. But intranets and extranets are limited in their physical distribution and by their security hardware and software.
The following paragraph discusses the networking systems for particular business needs.
Internet, Intranets, and Extranets
- Internet: Connects your employees to a global network so that they can search Web sites for information on global markets.
- VPN: Connects employees whose home machines are not part of your company's network to the corporate network so that they can work from home.
- Intranet: Provides a way for employees to learn information that is specific to the company and confidential to its members. A private network that is employed within the confines of a given enterprise (for example, internal to a business or agency).
- Extranet: Provides a way for a company's predetermined set of users from multiple organizations to exchange information and transact business over a shared Web site.
Extranet
An extranet is a computer network that allows controlled access from outside of an organization's intranet.
Extranets are used for specific use cases including business-to-business. In a business-to-business context, an extranet can be viewed as an extension of an organization's intranet that is extended to users outside the organization, usually partners, vendors and suppliers, in isolation from all other Internet users. In contrast, business-to-consumer (B2C) models involve known servers of one or more companies, communicating with previously unknown consumer users. An extranet is similar to a DMZ in that it provides access to needed services for channel partners, without granting access to an organization's entire network. Relationship to an intranet An extranet could be understood as an intranet mapped onto the public Internet or some other transmission system not accessible to the general public, but managed by more than one company's administrator(s).
For example, military networks of different security levels may map onto a common military radio transmission system that never connects to the Internet. Any private network mapped onto a public one is a virtual private network (VPN), often using special security protocols. For decades, institutions have been interconnecting to each other to create private networks for sharing information. One of the differences that characterizes an extranet, however, is that its interconnections are over a shared network rather than through dedicated physical lines.
A site can be in more than one VPN; for example, in an intranet and several extranets. We regard both intranets and extranets as VPNs. In general, when we use the term VPN we will not be distinguishing between intranets and extranets. Even if this argument is valid, the term "extranet" is still applied and can be used to eliminate the use of the above description.
The next lesson is about switches, bridges, and routers, which are the devices that interconnect the different kinds of networks.
A site can be in more than one VPN; for example, in an intranet and several extranets. We regard both intranets and extranets as VPNs. In general, when we use the term VPN we will not be distinguishing between intranets and extranets. Even if this argument is valid, the term "extranet" is still applied and can be used to eliminate the use of the above description.
The next lesson is about switches, bridges, and routers, which are the devices that interconnect the different kinds of networks.