| Lesson 7 | Authentication |
| Objective | Identify authentication methods. |
Authentication Methods
Authentication and certification both ensure the identity of the person or entity with whom you transact, but the methods they use are different: authentication proves who the parties are to one another, and certification uses an intermediary for proof.
Authentication through digital signatures is used in high risk e-commerce transactions, as well as for the delivery of highly sensitive information, even software. Authentication proves who the parties are to one another, and certification uses an intermediary for proof.
Let's review authentication and certification in more detail.
Authentication through digital signatures is used in high risk e-commerce transactions, as well as for the delivery of highly sensitive information, even software. Authentication proves who the parties are to one another, and certification uses an intermediary for proof.
Let's review authentication and certification in more detail.
Authentication
In the authentication process, the recipient of a message receives a digital signature. Because a digital signature can't be forged, the recipient can be confident of the sender's identity. The Slide Show below describes how authentication works.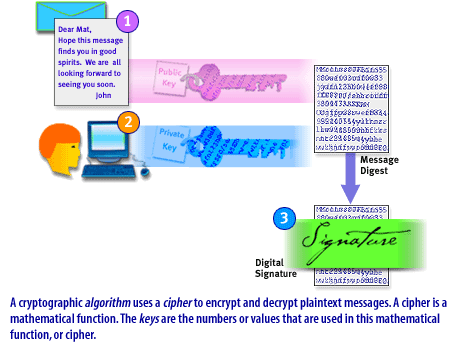
- A cryptographic algorithm uses a cipher to encrypt and decrypt plain text messages.
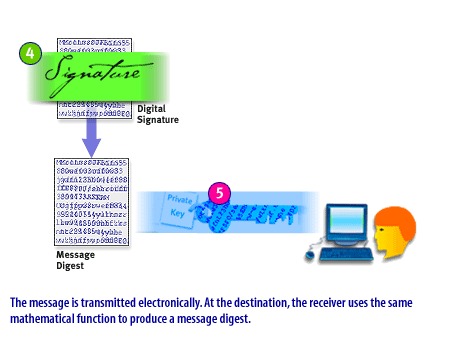
- The message is transmitted electronically.
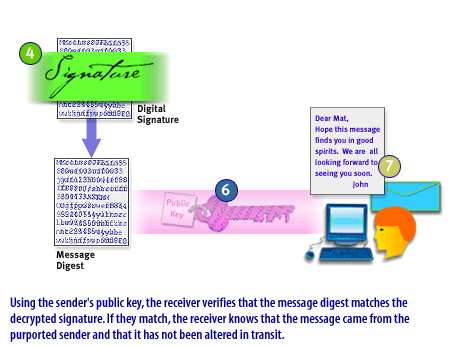
- Using the sender's public key, the receiver verifies that the message digest matches the decrypted signature



Asymmetric Cryptographic Algorithm
In the next lesson, you will identify various certification methods.