| Lesson 8 | Certification |
| Objective | Identify certification methods. |
Identify certification methods
Digital certificates are similarly applied to authentication techniques; the key difference with certificates is that a third party acts as the certificate provider. In a sense, certificates prove that someone else knows who you are, or who your partner is.Certification
Public-key encryption is based on the idea that an individual will generate a key pair, keep one component secret, and publish the other component. Other users on the network must be able to retrieve this public key, associate it with an identity of some sort, and use it to communicate securely with, or authenticate messages from, the user claiming that identity.Let us review certification in more detail.
How certification works One way to form an association between a key and a user is to enlist the services of a trusted third party. The third party will guarantee that a user is indeed who he or she claims to be as shown in the image below.
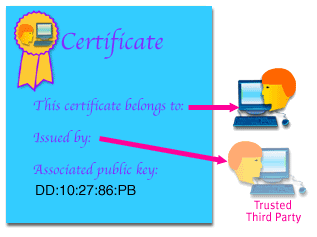
The third party guarantees a users identity by constructing a message, referred to as a certificate, that contains a number of fields, the most important of which are a user identity and the associated public key.
The trusted third party then signs this certificate using its private key, thereby guaranteeing that the public key is associated with the named user.
When is a certificate used? The certificate is used when the message recipient wants to gain access to the sender's public key. The recipient can either consult some online directory service to obtain this, or the sender may append his or her certificate to the message.
The issuers and managers of certificates are known as certificate authorities or CAs. The CAs are organized into a hierarchy to make them easier to manage. The root of the hierarchy is a CA that issues certificates to other CAs, which, in turn, certify the users of the system. Each system user need only hold the public key of the root CA. When sending a message, he or she includes a copy of all certificates in the path between himself or herself and the root.
When a certificate is revoked If a user's private key becomes compromised, or the certificate expires (because the user did not pay the monthly dues), the certificate associated with the public key is revoked. To completely trust the authenticity of the message, users must contact the CA for each certificate in the trust chain to ensure that none have been revoked.
Now apply what you have learned about digital certificates and certificate authority by completing the exercises below. The next lesson concludes this module.
Digital Certificate - Exercise
Click the Exercise link below to complete an exercise on digital certificates.
Digital Certificate - Exercise
Digital Certificate - Exercise