| Lesson 3 | Design for security |
| Objective | Describe security measures needed to protect your e-commerce site. |
Describe Security Measures needed to protect your ecommerce Website
A successful security system designed for an e-commerce site is a matrix, or a combination of individual methods, techniques, and subsystems. Whenever possible, you want to use as many security principles and techniques as possible to protect each resource.
For instance, a network that relies solely on authentication is not nearly as secure as one that combines authentication, access control, and encryption. Access control occurs if you apply packet filtering to the router. A firewall provides more access control.
In most e-commerce sites, a firewall is designed to provide access control more than anything else. If you supplement this with Secure Socket Layers (SSL) or Secure Electronic Transactions (SETs) at the Web server, you will be using encryption as well as authentication. Finally, an e-commerce site should always install intrusion detection software on mission-critical network segments and hosts.
For instance, a network that relies solely on authentication is not nearly as secure as one that combines authentication, access control, and encryption. Access control occurs if you apply packet filtering to the router. A firewall provides more access control.
In most e-commerce sites, a firewall is designed to provide access control more than anything else. If you supplement this with Secure Socket Layers (SSL) or Secure Electronic Transactions (SETs) at the Web server, you will be using encryption as well as authentication. Finally, an e-commerce site should always install intrusion detection software on mission-critical network segments and hosts.
- Authentication: Establishes a person's identity.
- Access control: Determines where a person or network host is allowed to enter a system.
- Encryption: Encryption is the process of transforming a file using a mathematical function or technique so that the contents of the file are protected from unwanted viewing.
- Packet filtering: The use of a type of firewall device that processes network traffic on a packet-by-packet basis. Packet filter devices allow or block packets, and are typically implemented through standard routers.
- Firewall: A firewall is a series of applications and hardware that filters and audits outside network traffic as it passes into your network.
Intrusion Detection
The key areas to secure are:
As shown in the MouseOver below, these key areas have particular risks associated with them.
- Local resources
- Network resources
- Server resources
- Database and information resources
As shown in the MouseOver below, these key areas have particular risks associated with them.
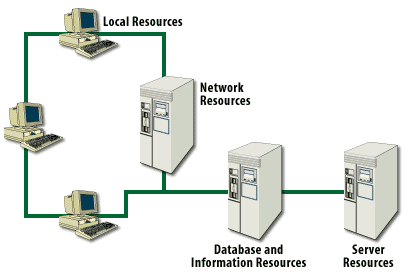
- Local resources - Protect your employee workstations by enabling password-protected screen savers to prevent snooping. Require that each employee use a virus checker and observe caution when downloading anything from the Internet.
- Network resources - Physically secure your routers, switches, and patch panels. Ensure that your DNS servers are free from tampering. If you have WINS or SAMBA servers internal to your e-commerce company, make sure that they are properly configured and secure. These network resources are the primary communication medium for the entire company. If a hacker gains access to or control of these elements, he or she has access to all or most company data.
- Database and information resources - A major asset of any company is the information it organizes and disseminates. A hacker's ultimate goal is to discover this information, as well as tamper with the networks and methods that help to create and communicate the information.
- Server resources - Your World Wide Web, email, and FTP servers are vulnerable to several types of intrusions. Typically, servers provide storage for the network infrastructure and act as the hub. They also control overall system security. Hackers try to gain access to server resources because they can then access and control other resources.
Protect Key Resources
The key means of achieving security are:
- Use cryptographic methods to provide data confidentiality, data integrity, and authentication
- Provide access control for all systems, servers, and files
- Secure CGI and other executable scripts
- Utilize virus scanning software and keep it up to date
- Combine security techniques to provide the best possible security. For example, connect the Web server to the database using a different protocol than TCP/IP
- Define a system security policy and security administration
- Train all users on security policies that apply to their jobs
- Build a firewall between your network and the Internet
- Monitor and analyze log files
CGI Scripts Web Search Engines
System attributes
The table below summarizes the most important attributes and goals of an effective security system for an e-commerce site.










- Allows access to only authenticated legitimate users
- Specific application should employ an intuitive interface
- Allows business to be conducted as needed
- Notifies the administrator quickly and in sufficient detail of a breach
- Planning includes initial purchase cost as well as costs for upgrades and service
System Attributes
In the next lesson, you will learn more about operating system security.
Resources Security Risks
Click the link below to review resources and security risks.
Resources Security Risks
Resources Security Risks