| Lesson 4 | Operating System Security |
| Objective | Design for e-commerce System Security at the Operating System Level. |
Operating System Security Design for e-commerce
Security Protection
Protection deals with protecting files and other resources from accidental misuse by cooperating users sharing a system, generally using the computer for normal purposes.
- Security deals with protecting systems from deliberate attacks from individuals intentionally attempting to steal information, damage information, or otherwise deliberately wreak havoc in some manner.
- Some of the most common types of violations include:
- Breach of Confidentiality: Theft of private or confidential information, such as credit-card numbers, trade secrets, patents, secret formulas, manufacturing procedures, medical information, financial information, etc.
- Breach of Integrity: Unauthorized modification of data, which may have serious indirect consequences. For example a popular game or other program's source code could be modified to open up security holes on users systems before being released to the public.
- Breach of Availability: Unauthorized destruction of data, often just for the "fun" of causing havoc and for bragging rites. Vandalism of web sites is a common form of this violation.
- Theft of Service: Unauthorized use of resources, such as theft of CPU cycles, installation of daemons running an unauthorized file server, or tapping into the target's telephone or networking services.
- Denial of Service, DOS: Preventing legitimate users from using the system, often by overloading and overwhelming the system with an excess of requests for service.
- One common attack is masquerading, in which the attacker pretends to be a trusted third party. A variation of this is the man-in-the-middle, in which the attacker masquerades as both ends of the conversation to two targets.
- A replay attack involves repeating a valid transmission. Sometimes this can be the entire attack, (such as repeating a request for a money transfer), or other times the content of the original message is replaced with malicious content.
Four Levels System Protection
There are four levels at which a system must be protected:- Physical: The easiest way to steal data is to pocket the backup tapes. Also, access to the root console will often give the user special privileges, such as rebooting the system as root from removable media. Even general access to terminals in a computer room offers some opportunities for an attacker, although today's modern high-speed networking environments provide more and more opportunities for remote attacks.
- Human: There is some concern that the humans who are allowed access to a system be trustworthy, and that they
cannot be coerced into breaching security. However, more and more attacks today are made by means of social engineering, which basically means fooling trustworthy people into accidentally breaching security.
A commonly used technique known as phishing involves sending an innocent-looking e-mail or web site designed to fool people into revealing personal or confidential information, which will enable the attacker to obtain access to several accounts by means of deception.
An example of this might be receiving spam e-mails pretending to be from ebay, PayPal or any of a number of banks or credit-card companies.- Dumpster Diving involves searching the trash or other locations for passwords that are written down. ( Note: Passwords that are too hard to remember, or which must be changed frequently are more likely to be written down somewhere close to the user's station. )
- Password Cracking involves deriving user passwords, either by watching them type in their passwords, knowing something about them like their pet's names, or simply trying all words in common dictionaries. ( Note: "Good" passwords should involve a minimum number of characters, include non-alphabetical characters, and not appear in any dictionary ( in any language ), and should be changed frequently.
Note also that it is proper etiquette to look away from the keyboard while someone else is entering their password. )
- Operating System: The OS must protect itself from security breaches, such as runaway processes (DOS: denial of service ), memory-access violations, stack overflow violations, the launching of programs with excessive privileges, and many others.
- Network: As network communications become ever more important and pervasive in modern computing environments, it becomes ever more important to protect this area of the system. (Both protecting the network itself from attack, and protecting the local system from attacks coming in through the network.) This is a growing area of concern as wireless communications and portable devices become more and more prevalent










- Assign the lowest level of access for each user or group that allows it to perform its job.
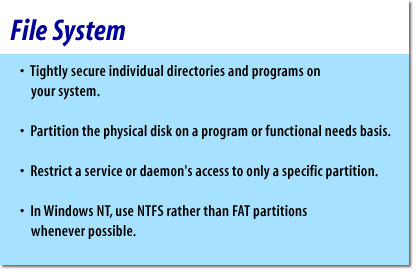
- Tightly secure individual directories and programs on your system
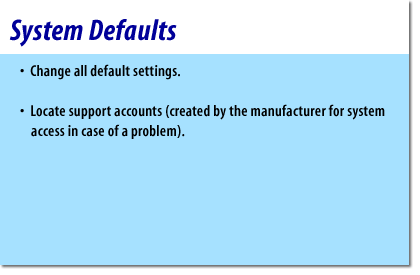
- Change all default settings
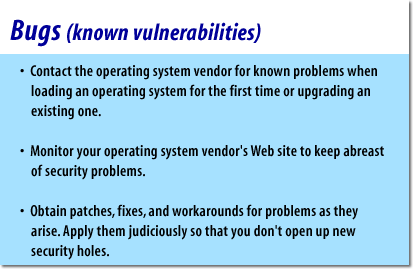
- Contact the operating system vendor for known problems when loading an operating system for the first time or upgrading an existing one
- Remove any operating system service that you do not specifically require.
- Operating System Specific 1) Implement security measures that are OS specific , such as securing the registry in Windows and enabling shadow password in UNIX systems
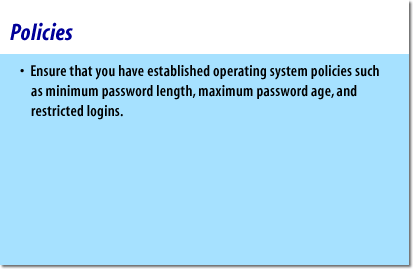
- Ensure that you have established operating system policies such as minimum password length, max password age, and restricted logins
Security Implementation Components
Remove unnecessary services that might create an unintentional back door.
Operating System Security Auditing
In the next lesson, you will learn about e-commerce system security at the server level.
Operating System Security Auditing
In the next lesson, you will learn about e-commerce system security at the server level.