| Lesson 2 | Security risks |
| Objective | Describe Security Risks |
Describe Security Risks and preventive Measures to be taken
The first objective for any e-commerce site is to assure clients or customers that their personal data remains private and safe as it passes across the Internet.
You also have to assure clients that personal information will remain private after it reaches your site. Security risks include attacks on middleware [1] common gateway interface (CGI) programs, credit card fraud, the generation of false orders, and virus and Trojan infiltration. These attacks are designed to expose confidential company information, which results in the loss of customer trust.
You also have to assure clients that personal information will remain private after it reaches your site. Security risks include attacks on middleware [1] common gateway interface (CGI) programs, credit card fraud, the generation of false orders, and virus and Trojan infiltration. These attacks are designed to expose confidential company information, which results in the loss of customer trust.
ecommerce Security, and hotmail
The primary security threats are shown in the MouseOver below.
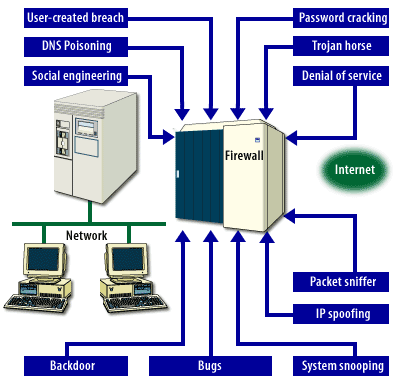
- Users may unknowingly create a security risk by using weak passwords, or by downloading a file containing a virus
- Dictionary programs specifically written to break into a password-protected system are frequently used to gain access to network systems.
- Users can inadvertently download destructive viruses and Trojan horses thereby compromising your network's ability to function. A "Trojan horse," or "trojan," is an illicit service that defeats authentication and access control measures.
- To prevent legitimate users of a service from using that service, attackers may attempt to flood a network, or disrupt connections or services.
- Sniffers, devices or programs that are used to monitor traffic on a network, can be installed anywhere in a networked system.
- Many hackers can imitate any Internet Protocol (IP) device that has an IP address that allows them entrance into your system.
- Using Transmission Control Protocol/Internet Protocol (TCP/IP), a hacker can enter your system through device that does not have specific security mechanisms in place.
- Many times, an operating system or program running on the server contains coding problems or bugs that create an unintentional opening. Hackers often know about such problems and exploit them.
- Program designers sometimes intentionally place a back door in an operating system or program so they can support the product quickly.
- A hacker may use tricks and disinformation to gain access to passwords and other sensitive information. For example, a hacker might imitate a legitimate user by confusing a switchboard operator or a guard.
- It is possible for a hacker to misdirect users to other sites. For example, hackers can send bogus information to a DNS server that may make someone else's site appear as it were yours.
Although there is no such thing as a completely secure site, you can achieve a sufficient level of security that the effort involved to penetrate the site exceeds the gain of doing so. This is the essence of successful Internet security. If the required effort to penetrate security costs more than the gain that results from doing so, perpetrators will seek out easier targets.
Security policy
A well-defined, well-written security policy [2] should be the foundation of your e-commerce site. This policy should include a private series of documents that discusses procedures for purchasing equipment, as well as procedures to follow in case of a break-in. The public series of documents has two purposes:
- To inform employees about accepted activity. This is often called an acceptable use policy (AUP).
- To inform customers about their expectations of privacy.
If you do not have a security policy in place, your company is unprotected. You should endeavor to publish this security policy in as many ways as possible, so that employees and clients have free access to it. Elements of your employee security policy may include the following best practices:
- Advice about protecting passwords. For example, employees should not write passwords down on sticky notes or under the keyboard.
- Stipulations about proper conduct in regard to email use and access to the World Wide Web.
- Directions for contacting individuals in case of a security breach.
- Authorized procedures for logging on to systems.
- Statements about acceptable and unacceptable software loaded on systems. For example, you could stipulate that a specific browser that must be used. You could even stipulate that only the IT department can load software on systems.
- Short examples of acceptable and unacceptable activities.
[1]Middleware: Software systems and utlities that provide a service and sit between the client and backend databases or legacy systems.
[2]Security policy: The foundational building block for a site's security.