Access Control Methods
In computer security, general access control includes authorization, authentication, and access approval.
A more narrow definition of access control would cover only access approval,
whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access.
Authentication and access control are often combined into a single operation, so that access is approved based on successful authentication, or based on an anonymous access token.
Authentication methods and tokens include passwords, biometric scans, physical keys, electronic keys and devices, hidden paths, social barriers, and monitoring by humans and automated systems.
Authorization is the process where requests to access a particular resource should be granted or denied. It should be noted that authorization is not equivalent to authentication because these terms and their definitions are frequently confused. Authentication is providing and validating identity. In a system that uses a simple username and password scheme, the authentication process collects the username and validates the identity using the password. Authorization is the execution of access control properties, ensuring the proper allocation of access rights once authentication is successful.
Access Control is the method of authorization to enforce that requests to a system resource or functionality should be granted.
We need to know that entities that request access to resources are subjects and the resource is an object. Unless otherwise designed to, web applications need access controls to allow users to use the applications and administrators to manage the application. To choose the most appropriate access control methodology, a risk assessment needs to be performed to identify threats and vulnerabilities, so that the identified methodology brings down the risk value to an acceptable level.
Authentication and access control are often combined into a single operation, so that access is approved based on successful authentication, or based on an anonymous access token.
Authentication methods and tokens include passwords, biometric scans, physical keys, electronic keys and devices, hidden paths, social barriers, and monitoring by humans and automated systems.
Authorization is the process where requests to access a particular resource should be granted or denied. It should be noted that authorization is not equivalent to authentication because these terms and their definitions are frequently confused. Authentication is providing and validating identity. In a system that uses a simple username and password scheme, the authentication process collects the username and validates the identity using the password. Authorization is the execution of access control properties, ensuring the proper allocation of access rights once authentication is successful.
Access Control is the method of authorization to enforce that requests to a system resource or functionality should be granted.
We need to know that entities that request access to resources are subjects and the resource is an object. Unless otherwise designed to, web applications need access controls to allow users to use the applications and administrators to manage the application. To choose the most appropriate access control methodology, a risk assessment needs to be performed to identify threats and vulnerabilities, so that the identified methodology brings down the risk value to an acceptable level.
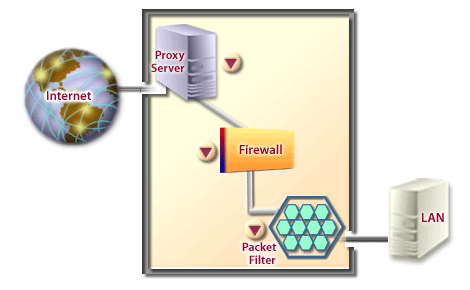
- A program that runs on the firewall as an intermediary between external clients and internal servers so that they do not connect directly.
- A combination of hardware and software that defends intranets against intruders by filtering inbound or outbound data, by authenticating users, and /or encrypting data.Firewalls can be custom assembled or purchased commercially.
- A filter that recognizes authorized addresses and designated types of traffic specified in an organization's security policy.. Packet filters discard unauthorized data packets.