VPN Security Techniques
Virtual Private Network
VPN is a generic term used to describe a communication network that uses any combination of technologies to secure a connection tunnelled through an otherwise unsecured or untrusted network.
Instead of using a dedicated connection, such as leased line, a "virtual" connection is made between geographically dispersed users and networks over a shared or public network, like the Internet.
Data is transmitted as if it were passing through private connections.
VPN transmits data by means of tunnelling. Before a packet is transmitted, it is encapsulated in a new packet, with a new header. This header provides routing information so that it can traverse a shared or public network, before it reaches its tunnel endpoint. This logical path that the encapsulated packets travel through is called a tunnel. When each packet reaches the tunnel endpoint, it is decapsulated and forwarded to its final destination. Both tunnel endpoints need to support the same tunnelling protocol. Tunnelling protocols are operated at either the
VPN transmits data by means of tunnelling. Before a packet is transmitted, it is encapsulated in a new packet, with a new header. This header provides routing information so that it can traverse a shared or public network, before it reaches its tunnel endpoint. This logical path that the encapsulated packets travel through is called a tunnel. When each packet reaches the tunnel endpoint, it is decapsulated and forwarded to its final destination. Both tunnel endpoints need to support the same tunnelling protocol. Tunnelling protocols are operated at either the
- OSI (Open System Interconnection)
- layer two (data-link layer), or
- layer three (network layer).
Vpn Security
VPN uses encryption to provide data confidentiality. Once connected, the VPN makes use of a tunnelling mechanism described above to encapsulate encrypted data into a
secure tunnel, with openly read headers that can cross a public network.
Packets passed over a public network in this way are unreadable without proper decryption keys, thus ensuring that data is not disclosed or changed in any way during transmission.
VPN can also provide a data integrity check. This is typically performed using a message digest to ensure that the data has not been tampered with during transmission. By default, VPN does not provide or enforce strong user authentication. Users can enter a simple username and password to gain access to an internal private network from home or via other insecure networks. Nevertheless, VPN does support add-on authentication mechanisms, such as smart cards, tokens and RADIUS.
VPN can also provide a data integrity check. This is typically performed using a message digest to ensure that the data has not been tampered with during transmission. By default, VPN does not provide or enforce strong user authentication. Users can enter a simple username and password to gain access to an internal private network from home or via other insecure networks. Nevertheless, VPN does support add-on authentication mechanisms, such as smart cards, tokens and RADIUS.
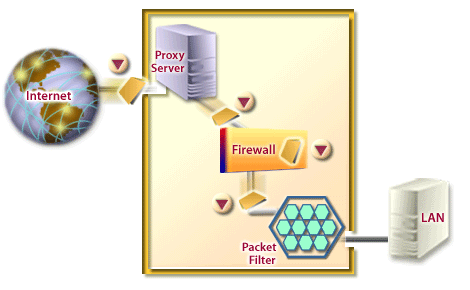
- The process of converting a legible message to an unreadable version able to be interpreted only by the sender and recipient.
- The process of verifying the identification of an entity such as a person or piece of software.
- A combination of hardware and software that defends intranets against intruders by filtering inbound or outboud data, by authenticating users, and by encrypting data.
- The process of transmitting data using a tunneling protocol that encapsulates encypted data in a secure container packet to be sent over the internet.