Packet Sniffers that can cause unacceptable Activities on your Network
An example of unacceptable activity in regard to e-commerce sites might include running special programs called "packet sniffers." In an e-commerce site, IT employees have a unique opportunity to eavesdrop on sensitive information, including passwords and credit card information. It is a good idea to state explicitly that such activities are expressly forbidden. The only exceptions to this rule should be when the senior IT manager has to scan the system as part of regular maintenance.
A packet analyzer (also known as a network analyzer, protocol analyzer or packet sniffer, or for particular types of networks, an Ethernet sniffer or wireless sniffer) is a computer program or a piece of computer hardware that can intercept and log traffic passing over a digital network or part of a network. As data streams flow across the network, the sniffer captures each packet and, if needed, decodes the raw data of the packet, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.
A packet analyzer (also known as a network analyzer, protocol analyzer or packet sniffer, or for particular types of networks, an Ethernet sniffer or wireless sniffer) is a computer program or a piece of computer hardware that can intercept and log traffic passing over a digital network or part of a network. As data streams flow across the network, the sniffer captures each packet and, if needed, decodes the raw data of the packet, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.
Host-based intrusion detection systems
Host-based IDSs are designed to monitor, detect, and respond to activity and attacks on a given host. In most cases, attackers target specific systems on corporate networks that have confidential information. They will often try to install scanning programs and other vulnerabilities that can record user activity on a particular host.
A host-based IDS allows an organization or individual owners of a host on a network to protect against and detect adversaries who may incorporate security loopholes or exploit other vulnerabilities. Some host-based IDS tools provide policy management, statistical analysis, and data forensics at the host level.
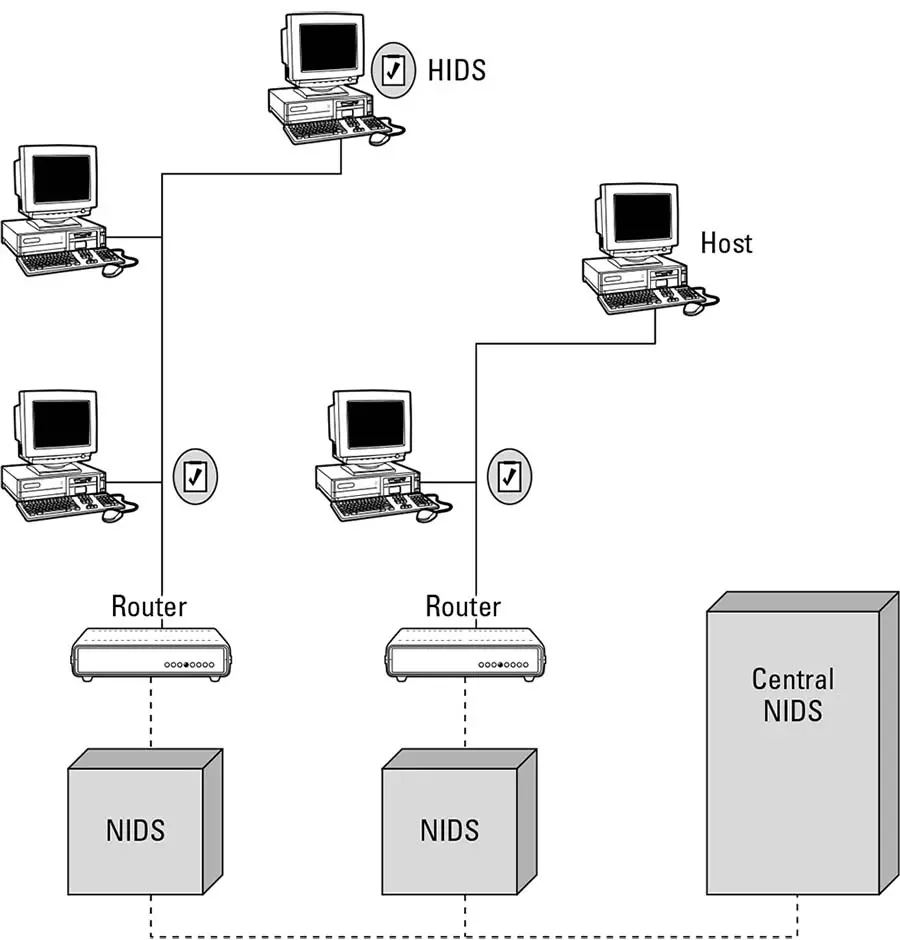
Host-based IDSs are best used when an intruder tries to access particular files or other services that reside on the host computer. In most cases, the host-based IDS is integrated into the operating systems that the host is running. Because attackers mainly focus on operating system vulnerabilities to break into hosts, such placement of the IDS proves very beneficial. Historically, many host-based IDSs were installed on the respective hosts themselves, because no separate intrusion detection entity could be provided for large mainframes (which needed much security) in a cost-effective manner. This method caused some security bottlenecks. An intruder able to successfully overcome the IDS and the inherent security features of the host could disable the IDS for further actions. Such disadvantages are overcome when the IDS is physically separated from the hosts themselves. With the advent of personal computers and cheaper hardware accessories, separate entities for placing IDSs are favored as show in figure 4-3.
Host-based IDSs are best used when an intruder tries to access particular files or other services that reside on the host computer. In most cases, the host-based IDS is integrated into the operating systems that the host is running. Because attackers mainly focus on operating system vulnerabilities to break into hosts, such placement of the IDS proves very beneficial. Historically, many host-based IDSs were installed on the respective hosts themselves, because no separate intrusion detection entity could be provided for large mainframes (which needed much security) in a cost-effective manner. This method caused some security bottlenecks. An intruder able to successfully overcome the IDS and the inherent security features of the host could disable the IDS for further actions. Such disadvantages are overcome when the IDS is physically separated from the hosts themselves. With the advent of personal computers and cheaper hardware accessories, separate entities for placing IDSs are favored as show in figure 4-3.
A network is only as secure as the weakest host connected to it.
Therefore, it follows that a host is only as secure as the weakest service that it is running. After all, the only way into a system from the network is through the services that it offers.
Because of this, a large part of network security involves ensuring that your services are configured securely. This entails configuring services to provide only the functionality that is required of them to accomplish the tasks they need to perform. Additionally, you should give services access to only the bare minimum of system resources needed.
That is just part of the solution, though. If a network service operates in clear-text, all of your work spent locking it down can be for nothing. In most cases, all an attacker has to do to gain access to such a service is use a packet sniffer to capture the login details of a user authenticating with the service. This chapter shows how to deploy IMAP, POP3, and SMTP servers that are protected with encryption, in order to prevent your users from accidentally disclosing their login credentials and keep their data safe from prying eyes.
Because of this, a large part of network security involves ensuring that your services are configured securely. This entails configuring services to provide only the functionality that is required of them to accomplish the tasks they need to perform. Additionally, you should give services access to only the bare minimum of system resources needed.
That is just part of the solution, though. If a network service operates in clear-text, all of your work spent locking it down can be for nothing. In most cases, all an attacker has to do to gain access to such a service is use a packet sniffer to capture the login details of a user authenticating with the service. This chapter shows how to deploy IMAP, POP3, and SMTP servers that are protected with encryption, in order to prevent your users from accidentally disclosing their login credentials and keep their data safe from prying eyes.