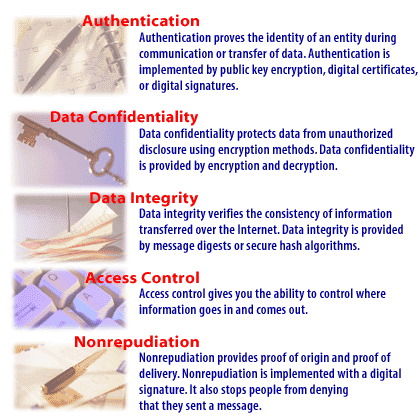
Security Services in ecommerce
Secure System
A secure system accomplishes its task with no unintended side effects. Using the analogy of a house to represent the system, you decide to carve out a piece of your front door to give your animals easy access to the outdoors. On the other hand, if the hole is too large, burglars may get access. You have created an unintended implication and therefore, an insecure system.
In the software industry, security has two different perspectives. In the software development community, it describes the security features of a system. Common security features are ensuring passwords that are at least six characters long and encryption of sensitive data. For software consumers, it is protection against attacks rather than specific features of the system. Your house may have the latest alarm system and windows with bars, but if you leave your doors unlocked, despite the number of security features your system has, it is still insecure. Hence, security is not a number of features, but a system process. The weakest link in the chain determines the security of the system.
In this article, we focus on possible attack scenarios in an e-Commerce system and provide preventive strategies, including security features, that you can implement. Security has three main concepts: confidentiality, integrity, and availability. Confidentiality allows only authorized parties to read protected information. For example, if the postman reads your mail, this is a breach of your privacy. Integrity ensures data remains as is from the sender to the receiver. If someone added an extra bill to the envelope, which contained your credit card bill, he has violated the integrity of the mail. Availability ensures you have access and are authorized to resources. If the post office destroys your mail or the postman takes one year to deliver your mail, he has impacted the availability of your mail.
In the software industry, security has two different perspectives. In the software development community, it describes the security features of a system. Common security features are ensuring passwords that are at least six characters long and encryption of sensitive data. For software consumers, it is protection against attacks rather than specific features of the system. Your house may have the latest alarm system and windows with bars, but if you leave your doors unlocked, despite the number of security features your system has, it is still insecure. Hence, security is not a number of features, but a system process. The weakest link in the chain determines the security of the system.
In this article, we focus on possible attack scenarios in an e-Commerce system and provide preventive strategies, including security features, that you can implement. Security has three main concepts: confidentiality, integrity, and availability. Confidentiality allows only authorized parties to read protected information. For example, if the postman reads your mail, this is a breach of your privacy. Integrity ensures data remains as is from the sender to the receiver. If someone added an extra bill to the envelope, which contained your credit card bill, he has violated the integrity of the mail. Availability ensures you have access and are authorized to resources. If the post office destroys your mail or the postman takes one year to deliver your mail, he has impacted the availability of your mail.
Dropshipping
Data Security in the Quantum Age
When you drill down in the world of quantum computing, you are confronted with a world that is not based on classical mechanics.
The concept itself upsets the calculator that is generally believed to underscore reality. However, there appears to be a deeper, more fundamental, and stranger layer to existence. In the atomic or subatomic realm, particles have been observed that are behaving in a way that conflicts with the physical laws as they have been traditionally defined, thus Einstein's famous description:
spooky action at a distance.From a computing standpoint, if a bit of data is either a 1 or a 0 in a classic computer, that same bit can be simultaneously a 1 and a 0 in the theoretical quantum computer. When very smart people build upon that revolutionary insight, they are naturally excited about the potential commercial applications of quantum computing. The most obvious application is in massively expanding the data-crunching capabilities of the worldwide digital ecosystem. As the data processing boundariesfor the Internet, cell phones, and payment systems continue to be pushed back, the demand for more processing power and speed only grows. Quantum computing has been touted as a solution to this demand. It might be a tad hyperbolic when scientists claim it would take a classic computer the size of the universe to perform as many computations as a single quantum computer, but it is the thought that counts.