| Lesson 5 | Server Security |
| Objective | Design for e-commerce system security at Server level |
Server level components to take into consideration when designing e-commerce system security
Database servers
The best option for securing database servers is to run them on a completely different system. You can then use a different network protocol, such as IPX/SPX or even NetBEUI, to establish communication between the Web server and the database. This arrangement allows full connectivity with the Web server but no direct connectivity from the Internet.
Middleware
Application servers and Java servlets can create security issues, mainly because they require extensive customization and because many are built from scratch. As your site implements middleware servers, take the time to learn about the workings of such servers so that you can change any defaults or address possible security problems on an individual basis.
Web servers
The key to securing the Web server is to segment the operating system, the Web server program, and the server's files on their own hard drive or partition. If a breach occurs, such segmentation will help limit a hacker's activity to specific hard drives, or even parts of hard drives, that are not essential to the rest of the system.
FTP servers
Securing the file transfer protocol (FTP)[1] server is similar to securing the Web server. The FTP server should be separated from the files it downloads by using partitions. Whenever possible, FTP user accounts and access options must be separated from those used to access the Web. The FTP server should not allow access to sensitive files.
FTP Server Security
In an e-commerce setting, focus on securing your server resources as shown in the Mouseover below. FTP Server Security
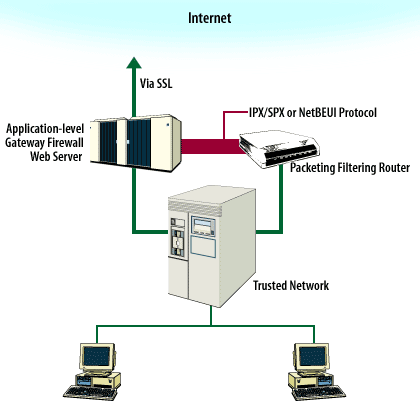
- A packet filtering router and an application gateway firewall should separate the trusted network from the Internet. These enforce access control as well as encryption and authentication. Intrusion detection software should be installed on the Web server and database.
- The Web server communicates with the outside world via SSL. The Web server and database should be communicating with each other via a different protocol than TCP/IP, such as IPX/SPX or NetBEUI, to help ensure the security of the database.
Securing Resources
Email servers
Simple Mail Transfer Protocol (SMTP): The Internet standard protocol to transfer electronic mail messages from one computer to another. It specifies how two mail systems interact, as well as the format of control messages they exchange to transfer mail.
Servers often offer security features, such as reverse domain name system (DNS) lookup, to help ensure that the email sender is actually who he or she claims to be. Advanced SMTP servers can scan email transparently by placing the email messages in a temporary holding area. Advanced virus scanners can search email attachments for malicious code. Such programs and servers scan the files, and then forward the email as appropriate.
Whenever possible, use such authentication[2] and access control measures. In the next lesson, you will learn about application security.
Whenever possible, use such authentication[2] and access control measures. In the next lesson, you will learn about application security.
Security Issues - Quiz
Click the Quiz link below to take a multiple-choice quiz on security issues.
Security Issues - Quiz
Security Issues - Quiz
[1] File transfer protocol: The File Transfer Protocol, or FTP, is the set of communication rules that computers use to exchange files.
[2] Authentication: Establishes a person's identity. Authentication is the act of confirming the truth of an attribute of a single piece of data claimed true by an entity.