| Lesson 5 | Security |
| Objective | Describe the impact of security on e-business. |
Security Impact on ebusiness
While corporate presence on the Web has soared, many companies are simply providing information about themselves in the form of annual reports, product catalogs, and service information. They have not begun to provide full-scale transactions for buying and selling online. This restraint is primarily due to concerns about network and transaction security.
Security Concerns and appropriate Technologies
Security concerns and the tools to address them generally fall into two areas--user authorization and data and transaction security.
This table clarifies these concerns.
Most eBusiness solutions need to realize a high level of security for both areas of concern, and as indicated in the table above, they use a range of technologies to do so. The most important security technologies are:
In this security technology, we will explain these technologies in greater detail.
| Area of concern | Explanation |
| User authorization | This ensures that only valid users and programs have access to resources like user accounts, files, and databases. |
| Data and transaction security | This ensures internal computers and databases from outside (Internet) access. |
Most eBusiness solutions need to realize a high level of security for both areas of concern, and as indicated in the table above, they use a range of technologies to do so. The most important security technologies are:
- Firewalls
- Encryption
- Biometrics
- Digital certificates
- SSL
- Public-key infrastructure (commonly called PKI)
In this security technology, we will explain these technologies in greater detail.

Question: What are the main security technologies discussed in this lesson?
Answer: Firewalls; Encryption; Biometrics; Digital certificates; SSL; Public-key infrastructure (PKI) If you would like to view and print out this information on security tools and their function, you may do so by looking at the information below.
The next lesson considers the issues to keep in mind when selecting any one of these security tools.
Answer: Firewalls; Encryption; Biometrics; Digital certificates; SSL; Public-key infrastructure (PKI) If you would like to view and print out this information on security tools and their function, you may do so by looking at the information below.
| Security Tool | How it works |
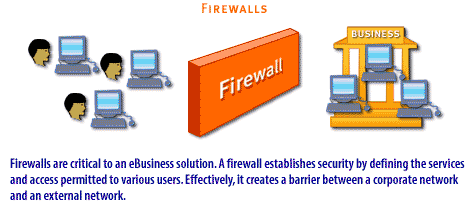
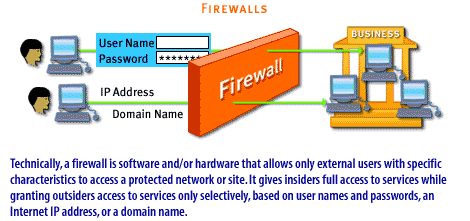
| Firewall | A firewall establishes security by defining the services and access permitted to various users. Effectively, it creates a barrier between a corporate network and an external network. Technically, a firewall is software and/or hardware that allows only external users with specific characteristics to access a protected network or site. It gives insiders full access to services while granting outsiders access to services only selectively, based on user names and passwords, an Internet IP address, or a domain name. |
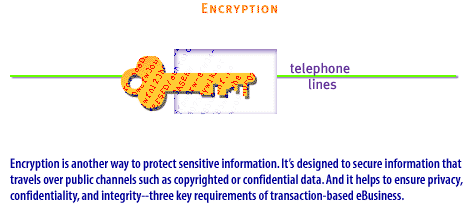
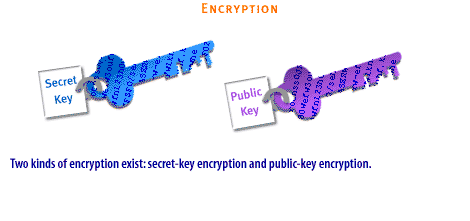
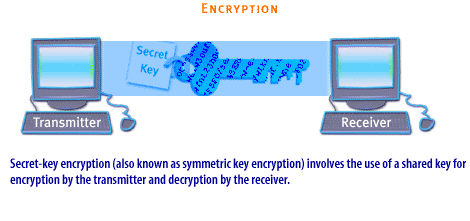
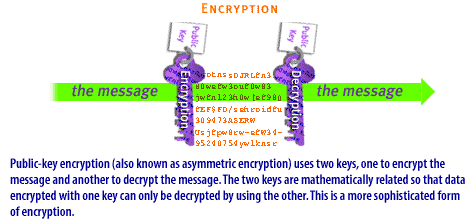
| Encryption | Encryption is designed to secure information that travels over public channels such as copyrighted or confidential data. It helps to ensure privacy, confidentiality, and integrity. Two kinds of encryption exist: secret-key encryption and public-key encryption:
|
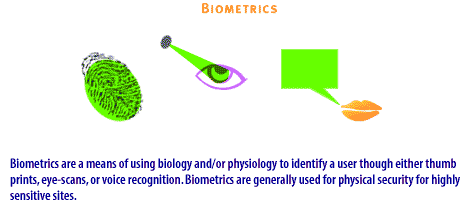
| Biometrics | Biometrics are a means of using biology and/or physiology to identify a user though either thumb prints, eye-scans, or voice recognition. They are generally used for physical security for highly sensitive sites. |
| Digital certificates | Digital certificates are attachments to electronic messages that are used for security purposes. They are one method of ensuring the identity of a person or entity in order to guarantee the integrity and to verify the origin of the user/order. |
| SSL | A Secure Sockets Layer (SSL) negotiates point-to-point security between clients and servers. By convention, Web pages that require an SSL connection start with https: instead of http:. |
| Public-key infrastructure (PKI) | PKIs are Internet-specific security suites that combine encryption technology, software, and services. They enable organizations to secure online business transactions and communication by integrating public-key cryptography and digital certificate technology into an organization-wide security infrastructure. |